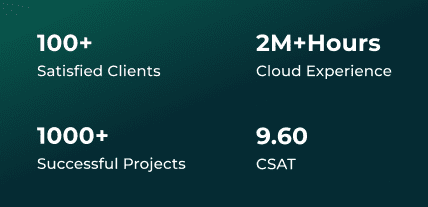
Why Mirketa
- Dedicated Pods for Your NOC: Persistent teams that learn your environment and SLAs
- Depth of Talent: Security engineers backed by cloud, platform, and SRE specialists
- Knowledge Retention: KEDB, playbooks, dependency maps, and shadowing to mitigate attrition risk
- Cost-Effective 24×7: Onshore governance with offshore scale; predictable pricing models
- Tooling-Agnostic: We run your stack accelerating time-to-value without disruption